BAT is a private application, completely inaccessible without the right credentials and permissions. It is known as Software as a Service SaaS. That means we do not operate a platform, do not have the infrastructure of server rooms and do not store your information on site. A third-party provider hosts applications and BAT writes the code-script.
To ensure information security, in Broker Admin Technology Ltd. we always work with the last released technologies, updates and patches.
The biggest difference between BAT and other applications in the Market, is that it doesn’t depend on any built-in code or content management system. All code has been written from scractch by our developers, always ensuring the highest quality standards in clean coding and security. To repeat in plain language: there are no “off the shelf” applications that could contain known weaknesses.
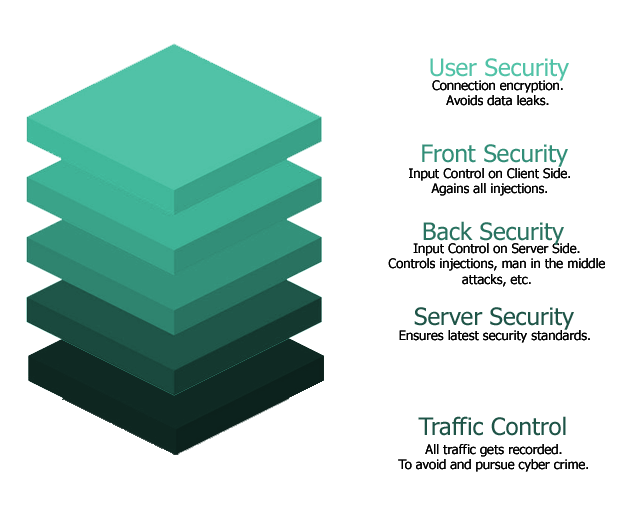
User Security
On the first layer, all the connections and correspondence between BAT and every user are encrypted connections. This prevents unwanted sensitive data leaks.
In addition, we also encrypt all the information being sent to the server and we store it – again encrypted – and this time with unique keys only known by our developers. The encrypted code prevents the information from being understood even if somehow the unique keys were stolen from those same developers.
Front Security
Every input on the application gets double checked on client side to avoid any kind of code injection. All recognised codes or unwanted symbols (such as hyperlinks contained in Word documents, for instance) are automatically deleted from inputs generally resulting in a controlled error display or just a blocked action.
Back Security
BAT back code checks every input and connection once again to avoid unwanted or harmful inputs.
Any input containing dangerous script will be kept away from code processing, as it gets filtered and cleaned before processing.
Server Security
We run weekly updates on every Server module, and we also upgrade to any new security standard as it becomes available to keep all systems up to date with current cyber security discoveries.
Traffic Control
Our application stores records for all user and machine connections made to it. Not only does this ensure security but it also allows us to pursue any attempted cyber attack and assist law enforcement with tracking sources. Under various provisions of The Computer Misuse Act (CMA) of 1990, Regulation of Investigatory Powers Act (RIPA) 2000, and GDPR 2018 it constitutes a crime in the United Kingdom to attempt to hack information.
We also monitor traffic activity using Security Information and Event Management SIEM to shorten our response times to a cyber attack.
